
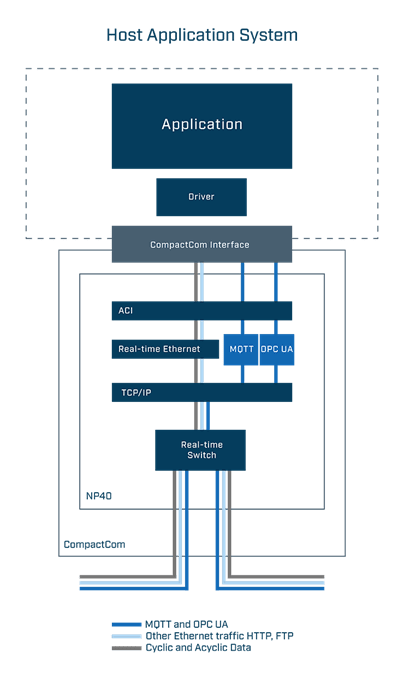
The Anybus CompactCom IIoT Secure enables your industrial devices to communicate using OPC UA and MQTT.
The Anybus Compact IIoT Secure exchanges industrial Ethernet protocol data (for example, PROFINET or EtherNet/IP) with the controller as usual but also uses the OPC UA or MQTT protocols to send data to IT systems. Companies can then analyze the data without needing to develop custom software.
OPC UA on CompactCom
The Anybus CompactCom uses the OPC UA Device Integration (DI) model to implement an OPC UA server in the device’s address space. The OPC UA server models the customer’s device as a device. The application will enable the OPC UA functionality where the ADIs (application parameters) are readable as variable nodes through OPC UA. The modelled device is of type CompactCom40DeviceType which is a subtype of the OPC UA DeviceType.
MQTT on CompactCom
The Anybus CompactCom acts as a publisher on the network using data from the host application. The data will be encoded using an encoding technology chosen by the host application before published, JSON or transparent encoding is supported. Data is tagged with a topic string that is used by the clients that would like to receive the data published by a device when subscribing for the data from the broker.
Security Chip
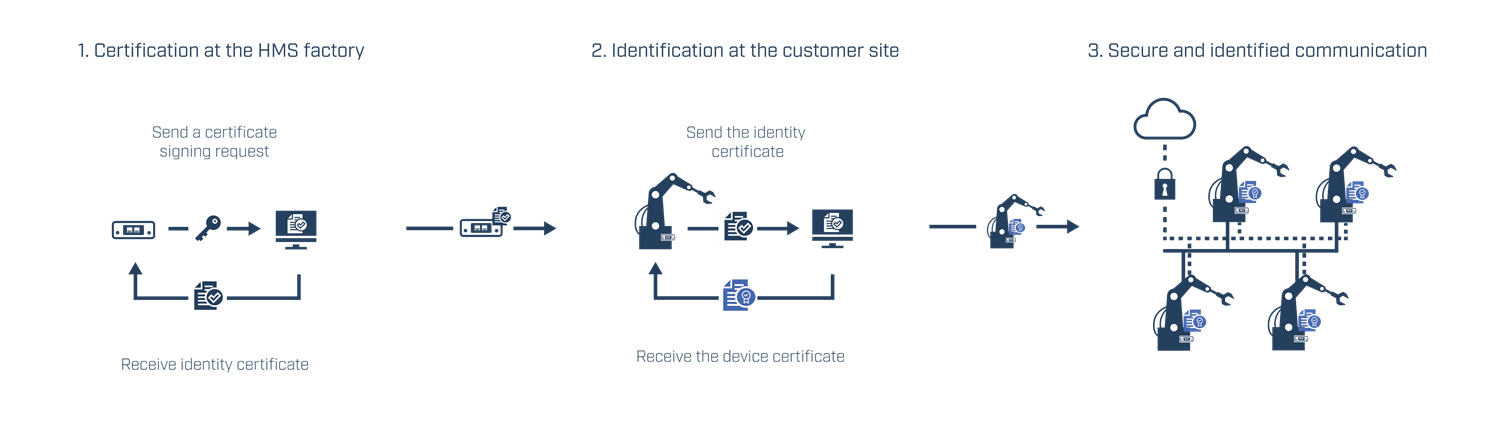
Secure Boot
Certificate Management
Encryption
Security is an ever ongoing process and HMS Networks continually test the Anybus CompactCom 40-series products to check resistance against packet storms, known security holes and malformed packets. Some of the methods and tools we use in different development projects are Achilles, Netload and Nessus.
To prevent unauthorized or malicious code from being downloaded, the CompactCom 40-series only accept firmware that has been digitally signed by HMS. The included FPGA design is encrypted. Using our own technology, we are in full control of the design, allowing us to optimize performance and fix possible vulnerabilities easily. Unused protocols and functionality can be disabled as necessary by the host application.